- Distribution Method : Automatic infection using exploit by visiting website
- MD5 : d410ad89fe5e0350e648ac39308fd848
- Major Detection Name :Trojan/Win32.Magniber.R215116 (AhnLab V3), Trojan.Win32.MyRansom.131072 (ViRobot)
- Encrypted File Pattern : .ypail
- Malicious File Creation Location :
- C:Users%UserName%AppDataLocalREAD_FOR_DECRYPT.txt
- C:Users%UserName%AppDataLocalypail.exe
- C:Users%UserName%Desktop<Random>.exe
- C:WindowsSystem32Tasksypail
- C:WindowsSystem32Tasks<Random>
- C:WindowsSystem32Tasks<Random>1
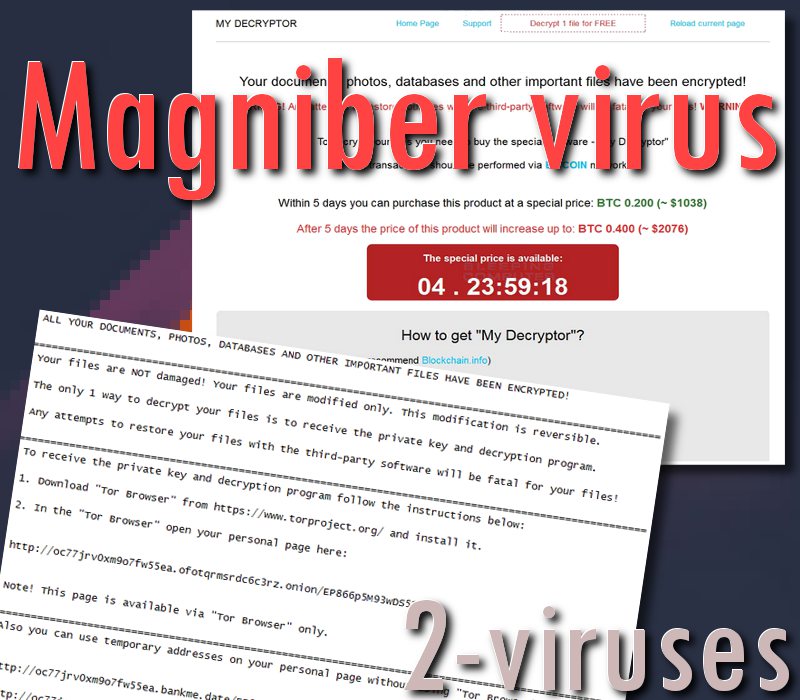
Ahnlab Magniber Decrypt V4
If AhnLab cannot assist with the variant you are dealing with, then unfortunately there is no other known method that I am aware of to decrypt files encrypted by Magniber without paying the ransom. How to remove Magniber virus and restore encrypted files. This article is dedicated to ransomware called Magniber which gets onto customers' machines around the world, and encrypts their files. Here we've assembled full info on Magniber's essence, and the deletion of Magniber from your system.
- Payment Instruction File : READ_ME_FOR_DECRYPT.txt
Ahnlab Magniber Decrypt V4.1

- Major Characteristics :
- Offline Encryption
- Only run on Korean operating system
- Change the default values of the registry entry 'HKEY_CLASSES_ROOTmscfileshellopencommand' and disable system restore (wmic shadowcopy delete) using Event Viewer (eventvwr.exe)
- Auto execute ransomware (pcalua.exe -a C:Users%UserName%AppDataLocalypail.exe -c <Random>) and payment instrucition file (%LocalAppData%READ_FOR_DECRYPT.txt) every 15 minutes by adding Task Scheduler entries
- Auto connect MY DECRYPTOR site (cmd.exe /c start iexplore http://<URL>) every a hour by adding Task Scheduler entries